In organizations, assets are given default rights, which are subsequently maintained by IT teams.
These rights can, however, constitute a serious danger to the organization since hackers might utilize the related privileged accounts to obtain vital credentials and abuse these privileges.
Companies can put in place a proactive privileged account management (PAM) procedure to handle this issue. IT managers can keep an eye on and control privileged accounts inside an organization with the help of a good PAM solution. This solution can be implemented as cloud-based, SaaS, or on-premise software.
Least privileged access (LPA) policies, which provide users the minimal access required to complete their duties, can be implemented as part of a PAM solution to assist reduce risks.
Thus, the remedy can aid in averting both internal and exterior hazards. To prevent such a troublesome circumstance, you must implement a privileged access control system.
In this article, we’ll examine privileged access management and the best options available.
So, what is Privileged Access Management?
A security mechanism known as privileged access management (PAM) enables organizations to manage and keep an eye on the activities of privileged users, including their access to vital business systems and what they can do once signed in.
Most businesses classify their systems into categories based on how serious the implications would be if a breach or abuse occurred.
Admin levels of access to high-tier systems are provided through privileged accounts, such as domain admin and networking equipment accounts, depending on higher degrees of permissions.
Although there are numerous strategies for managing privileges, the application of least privilege, which is defined as limiting access rights and permissions to the bare minimum required for users, accounts, applications, and devices to carry out their regular authorized tasks, is a key goal.
PAM is regarded by many analysts and engineers as one of the most important security approaches for lowering cyber risk and maximizing return on security expenditure.
Vendors of solutions for privileged access management assist administrators in regulating access to crucial company resources and ensuring the security of these top-tier systems. Critical business systems are protected by this additional security layer, which also promotes improved governance and data legislation compliance.
How does Privileged Access Management work?
Certainly! A cybersecurity solution called Privileged Access Management (PAM) has been developed to monitor and restrict privileged access to important systems, data, and applications.
Basically, it aids organizations in making ensuring that only authorized individuals are given access to sensitive data and systems and that this access is tracked and managed.
PAM functions by putting in place a series of security measures intended to prohibit unauthorized access to privileged accounts. This is accomplished by imposing rules that demand users to provide identification proof, go through multi-factor authentication, and finish access request procedures before being allowed access to privileged accounts.
PAM systems monitor user activity after access has been given and provide alarms when any questionable behavior is found. This can entail keeping track of every user behavior, seeing any odd trends, and immediately denying access to anybody who breaches access regulations.
By automating the password-rotation process, enforcing complicated password regulations, and offering a centralized view of all privileged accounts in the organization, PAM systems can also assist organizations in managing privileged accounts.
Privileged Access Management (PAM) Solutions
1. ManageEngine PAM360
For businesses that wish to integrate PAM into their security operations, PAM360 is a comprehensive solution. With the help of PAM360’s contextual integration features, you can build a central console that connects various components of your IT management system for a deeper correlation between privileged access data and overall network data, enabling more insightful conclusions and quicker repair.
No privileged access channel to your mission-critical assets escapes management, knowledge, or monitoring thanks to PAM360. It offers a credential vault where you can store privileged accounts to make this feasible.
This vault supports AES-256 encryption, role-based access controls, and centralized management. PAM360 restricts access to elevated privileges for domain accounts only when users actually require them. Permissions are automatically revoked and credentials are reset after a predetermined amount of time.
In addition to controlling privileged access, PAM360 enables privileged users to connect to distant hosts with only a single click, without the need for endpoint agents or browser plug-ins. This feature offers a network of connections that travel via password-free, encrypted gateways to offer the highest level of security.
Pricing
The premium pricing of the software starts from $7,995.
2. Cyberark
One of the greatest market shares for PAM is held by CyberArk, which provides enterprise-level, policy-driven solutions that let IT teams secure, monitor, and track privileged account activity.
Their Core Privilege Access protection (PAS) solution offers privileged accounts multi-layered access protection and includes over 500 “out of the box” connectors.
To find privileged access, Core PAS continually monitors the network.
Depending on the company’s policies, IT teams can decide whether to automatically cycle accounts and credentials or to check access attempts by adding them to a queue. Critical asset access credentials are kept separate in a safe vault, reducing the risk of credential disclosure.
IT teams have the option to record and audit restricted sessions in an encrypted repository via the central administration panel. Admins can observe particular keystrokes and actions recorded during video replay and keep an eye out for any suspicious conduct.
Core PAS automatically suspends or terminates the privileged session if suspicious behavior is found, depending on the level of risk. On suspension or termination, automatic credential rotation guarantees that unauthorized users or compromised inside accounts cannot regain access to the system.
With choices for on-premises, cloud, and SaaS deployment, CyberArk’s solution can be used by any organization, regardless of where they are in the cloud migration process.
Pricing
Please contact the vendor for its pricing.
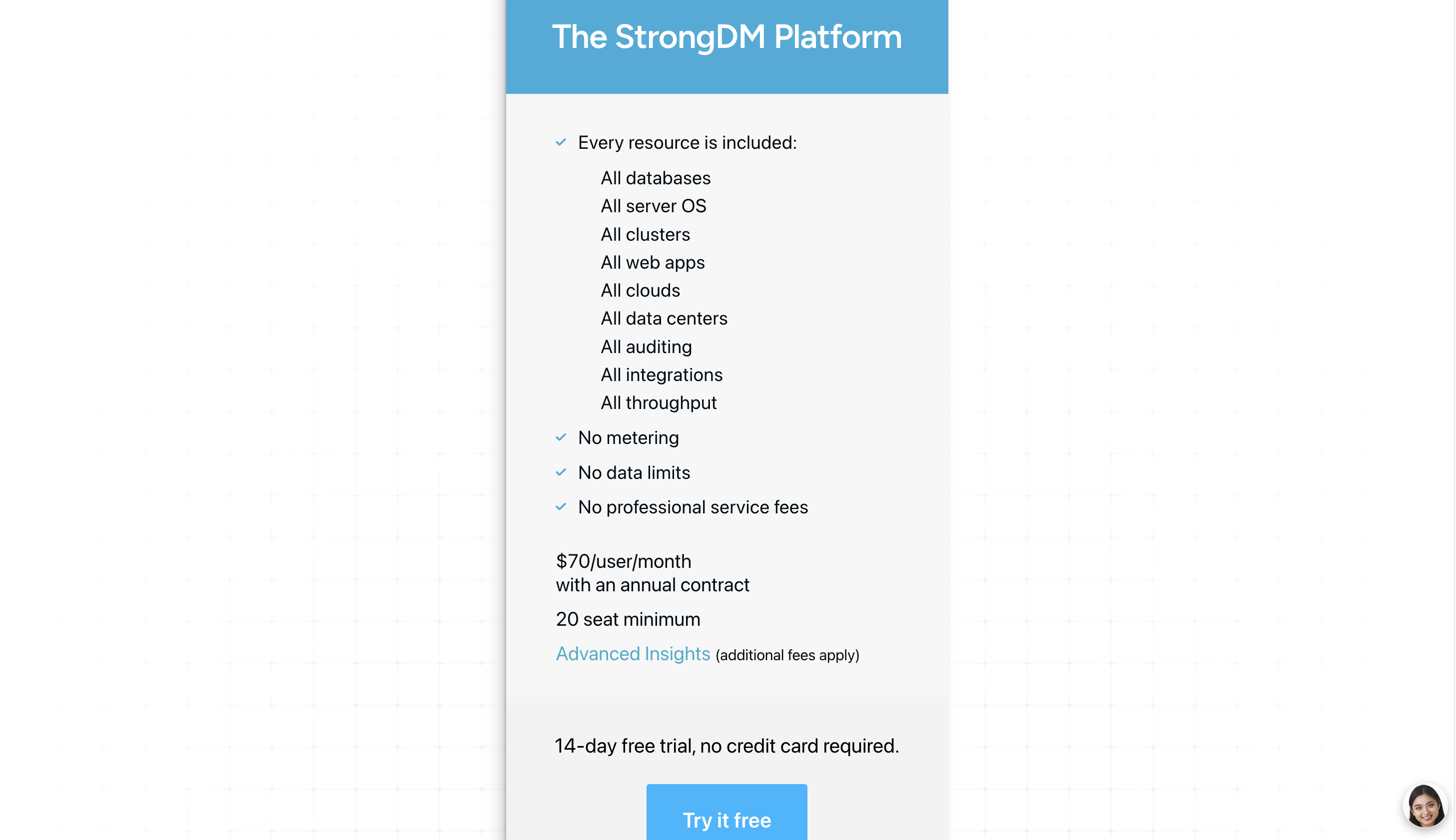
3. StongDM
In place of endpoint solutions, StrongDM provides an infrastructure access platform that supports all protocols. It is a proxy that integrates authentication, authorization, observability, and networking technologies into a single platform.
StrongDM’s permission assignment processes simplify access rather than speed it up by instantly granting and revoking granular, least-privilege access via role-based access control (RBAC), attribute-based access control (ABAC), or endpoint approvals for all resources.
Employee onboarding and offboarding can both be finished with a single click. Using PagerDuty, Microsoft Teams, and Slack for critical tasks now has the temporary authorization of privileged access.
StrongDM gives you the ability to connect any end user or service to the specific resources they require, wherever they can be. Additionally, bastion hosts and VPN access are replaced by zero-trust networks.
StrongDM provides a variety of automation options, such as the capacity to feed logs into your SIEM, include access controls into your current deployment process, and gather information for a range of certification audits, including SOC 2, SOX, ISO 27001, and HIPAA.
Pricing
You can try out the platform with its 14-day free trial, and premium pricing starts from $70/user/month with an annual contract.
4. JumpCloud
The Open Cloud Directory Platform from JumpCloud securely links privileged users to vital systems, programs, data, and networks. JumpCloud gives privileged accounts complete visibility and control.
It enforces strong authentication, allowing administrators to demand Multi-Factor Authentication (MFA) before access is granted, and it is natively integrated with our single sign-on (SSO) capabilities, allowing administrators to set precise policies governing what resources privileged accounts and individual users can access with their identities.
Strong password and SSH Key management is another feature of the JumpCloud Open Directory Platform that enables administrators to establish precise limits on the difficulty of passwords for privileged accounts and get notifications when these passwords are about to expire or are the target of brute force attacks.
With the help of JumpCloud’s device management features, administrators can alert privileged users to rotate their passwords at predetermined intervals, which then updates passwords and access across all of their MacOS, Windows, and Linux devices automatically.
This lowers the risk of static passwords, credential phishing, and other methods used to target privileged users.
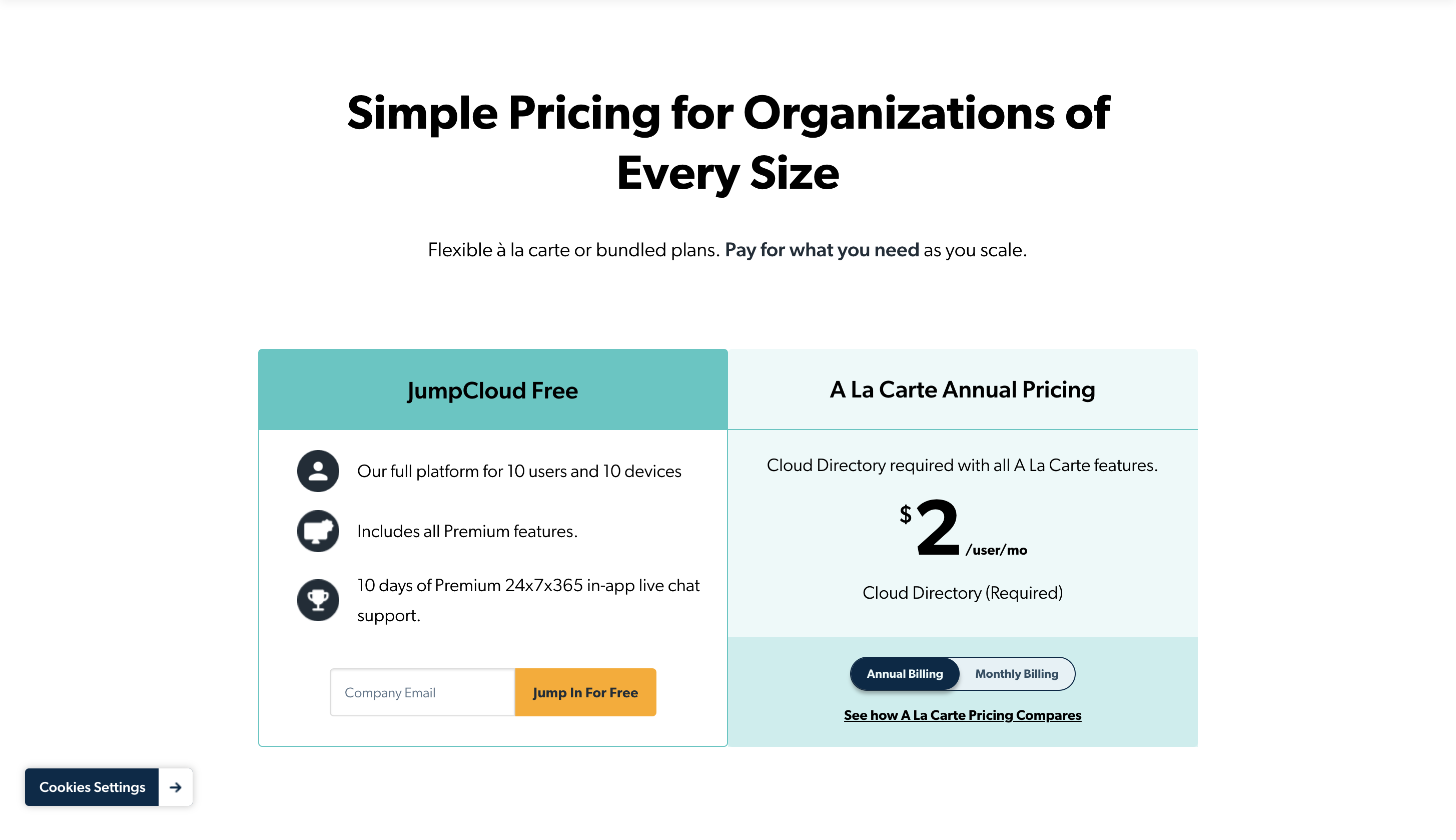
Pricing
You can start using it for free and premium pricing stats from $2/user/month.
5. ARCON
ARCON’s risk-management solutions are designed to protect data and privacy by anticipating risk situations, protecting organizations from those risks, and preventing events from occurring.
It makes it possible for security teams employed by businesses to protect and manage privileged accounts for their entire lifetime.
It protects against both insider assaults using privileged credentials and cybercrime from outside parties. Regular password changes are automated using ARCON’s safe password vault.
Strong, dynamic passwords that can only be accessible by authorized users are generated and stored in the vault. To access the vault, users must use multi-factor authentication (MFA).
If a company wants to add additional levels of authentication around the vault, ARCON provides native software-based one-time-password (OTP) validation that can be used to confirm users’ identities.
Due to the security of MFA, ARCON | PAM is able to perform single sign-on (SSO) access to all crucial systems without requiring users to divulge their login information.
As a result, the sign-on procedure is more effective, and vital data is shielded from the risk of password leaks.
Pricing
Please contact the vendor for its pricing.
6. Heimdal
With Heimdal Privileged Access Management, system administrators have the ability to quickly accept or reject requests for privilege escalation.
IT teams can completely design their environment in accordance with business demands while also saving significant time and money by developing automated escalation request approval pipelines that adhere to preset rules and constraints.
Enterprises can achieve complete NIST AC-5 and AC-6 compliance by incorporating Heimdal’s PAM solution into the infrastructure.
Users can access a complete audit trail with detailed escalation and de-escalation data that is available for 90 days using Privileged Access Management. Additionally, administrators can restrict their view of the information that has been logged to meet a variety of criteria, including requests, users, and more.
Last but not least, it is significant to note that Heimdal Patch & Asset Management is the only privileges escalation and delegation solution on the market that immediately de-escalates requests if a danger is detected. This is made feasible by combining PAM with other Heimdal suite products, specifically Heimdal’s Next-Gen Antivirus.
Pricing
You can try it with its free trial version and please contact the vendor for its pricing.
7. Foxpass
Foxpass Privileged Access Management automates network and server access, safeguarding crucial business systems while easing the burden on an IT team’s resources.
Customers can quickly configure their protection thanks to the system’s ability to effortlessly interface with any current systems in an organization, such as cloud mail systems and SSO programs.
Self-service administration of SSH keys, passwords, and MFA is available with Foxpass Privileged Access administration. Through a simple interface, administrators can define password requirements.
Additionally, the solution provides a complete API that admins can use to automate server access control, modify user information, and govern group memberships.
The API keeps track of all authentication requests so that administrators can easily see who is logging into crucial systems. These logs can also be used to demonstrate compliance.
Foxpass PAM can deliver single sign-on across an organization’s complete application stack, eliminating the need for passwords, thanks to cloud-hosted LDAP and RADIUS. At this level, administrators can additionally activate MFA for increased security as well as logging for LDAP and RADIUS requests for automatic threat detection and reaction.
Enterprise-grade security is provided by Foxpass’ PAM solution, which is also highly scalable and accessible both on-premises and in the cloud. Additionally, it smoothly connects with currently available third-party applications like Microsoft 365 and Google Workspace.
Pricing
You can try it with its 30-day free trial version and premium pricing starts from $3/user/month.
8. Delinea
Privileged access management software from Delinea is made to assist businesses in controlling and securing access to their most private corporate databases, apps, hypervisors, security tools, and network hardware.
It attempts to make installing and using the utility as simple as possible. The business simplifies its products to make access boundaries easier to define. Delinea’s PAM solutions are easy to deploy, configure, and administer without sacrificing functionality, whether in cloud or on-premises situations.
Delinea provides a cloud-based option that enables installation on millions of computers. A Privilege Manager for desktops and a Cloud Suite for servers make up this solution.
It identifies computers, accounts, and programs with administrator permissions on workstations and cloud-hosted servers by using Privilege Manager.
Even separate domain-specific computers can run it. It can handle privileges automatically by defining local group membership permanently and automatically rotating non-human privileged credentials by specifying rules.
With only a few clicks, you can elevate, refuse, and limit apps using a policy wizard. The reporting tool from Delinea also offers comprehensive data on the least privileged compliance and programs prohibited by malware. Additionally, it provides a connection between Privilege Manager Cloud and Privileged Behaviour Analytics.
Pricing
Please contact the vendor for its pricing.
9. Beyond Trust
A market leader in privileged access management is BeyondTrust. They provide a variety of solutions for endpoint, server, cloud, DevOps, and network device scenarios that enable high levels of visibility and security.
Without the need for a VPN, BeyondTrust’s Privileged Remote Access solution allows for the management and auditing of internal and external remote privileged access. No matter where they are, employees can be productive thanks to this solution, which also prevents malicious users from getting access to vital corporate systems.
Passwords are kept in a safe cloud-based on-appliance vault via Privileged Remote Access. As an alternative, BeyondTrust’s Password Safe, which is distributed as software, is integrated with this solution.
With any choice, BeyondTrust is able to securely inject credentials from the vault into a session. This feature is known as a credential injection. This implies that users never reveal their credentials while logging in.
Strong monitoring tools are also included in the system, and tracking and auditing functions are all available from a single interface.
Administrators can customize permission and notification settings to get notifications when a user accesses Privileged Remote Access.
Admins can accept access requests and check on use on their mobile devices from anywhere thanks to these alerts’ remote worker friendliness.
The usage of privileged accounts can be reviewed and tracked by IT teams, who can also provide reports to demonstrate compliance, thanks to thorough audit trails and session forensics.
Pricing
Please contact the vendor for its pricing.
10. Teleport
A Privileged Access Management (PAM) tool called Teleport is intended to give secure access to crucial infrastructure for staff members, independent contractors, and third-party suppliers.
With this approach, every infrastructure will be accessible to software developers and the apps they produce via a single platform.
This single platform claims to reduce the risk of security breaches by cutting operational expenses and attack surfaces while boosting productivity and ensuring standards compliance. This open-source approach replaces shared credentials, VPNs, and antiquated privileged access control techniques.
It was specifically designed to provide the necessary access to the infrastructure without obstructing work or decreasing the productivity of IT staff.
Engineers and security experts can leverage a single tool to connect to Linux and Windows servers, Kubernetes clusters, databases, and DevOps tools like CI/CD, version control, and monitoring dashboards.
Open standards are used by Teleport Server Access, including X.509 certificates, SAML, HTTPS, and OpenID Connect. Its designers concentrated on ease of installation and usage because these are the cornerstones of a positive user experience and a strong security policy.
It therefore only has two binaries: the Teleport agent, which can be deployed on any Kubernetes server or cluster with a single command, and a client that users can log into to receive temporary certificates.
Pricing
You can use the commercial version which is free for everyone and please contact the vendor for enterprise pricing.
Conclusion
In conclusion, platforms for Privileged Access Management (PAM) are crucial solutions for protecting access to sensitive information and vital infrastructure.
PAM solutions give businesses the power to regulate and watch over privileged access, lowering the danger of data breaches, cyberattacks, and insider threats.
Organizations can manage and keep track of privileged accounts using a PAM platform, which also enforces access limits and offers a centralized view of all privileged access activities.
These solutions can also enforce complicated password regulations, automate the password management process, and provide real-time monitoring and reporting.
PAM platforms are quickly becoming a crucial component of the cybersecurity toolset because of the rise in cyberattacks and data breaches.





Leave a Reply