Table of Contents[Hide][Show]
The cyber threat landscape for businesses is varied and developing quickly.
The creation of new tools and methods to get beyond the defenses that organizations put in place is a continuing effort of cyber threat actors. An organization could experience a ransomware infestation, data breach, or another negative security issue as a result of success.
By giving businesses knowledge about the most recent attack campaigns and trends in the cyber threat landscape, threat intelligence can help an organization anticipate and avoid assaults.
Analysts struggle to manually analyze threat data and derive insights quickly enough to be useful due to the sheer volume of accessible data.
The procedure for gathering, examining, and disseminating threat intelligence data is automated by a TIP. An organization can make sure that its defenses use the finest information available by employing a TIP to detect and stop prospective assaults.
Threat intelligence systems are made to collect data, examine patterns, and then give your company useful information about cybersecurity risks.
In order for this information to be current, it must be gathered as soon as possible. Your organization can address dangers before they escalate in harm by using this precise intelligence.
This article will examine the top threat intelligence platform that can be used within your company.
What is a threat intelligence platform?
A threat intelligence platform is a sort of cybersecurity tool that aids in finding, gathering, aggregating, organizing, and analyzing threat intelligence from multiple online sources, including the deep web, dark web, and clear web.
Utilizing a TIP, you can gather useful information from several sources in a variety of forms, and then apply cutting-edge algorithms and machine learning to analyze the data.
You can find indications of compromise (IOCs) by doing this, which can assist you in stopping assaults before they begin.
The most fascinating aspect of cutting-edge TIP systems is that they also incorporate human intelligence obtained by cybersecurity experts who connect with threat actors where they plot attacks and trade stolen and leaked data.
Security teams can identify new threats from well-known malware attack types using the data found and revealed by a TIP, as well as preparations for upcoming assaults.
With this knowledge, they can take preventative risk management measures and corrective action to stop those assaults from happening in the first place.
Threat Intelligence platforms
1. IBM Security X-Force
Businesses searching for strong threat intelligence capabilities can consider IBM since it is a leading provider of hardware, middleware, and software globally.
You can quickly find, analyze, prioritize, and fix issues on a single user-friendly platform with the help of the Threat Intelligence Insights application, which is a part of the IBM Cloud Pak for Security and also includes applications like its data explorer, SOAR, risk manager, and Guardium insights.
The built-in features of IBM Security X-Force are also jam-packed with awesome capabilities, such as a personalized Threat Score that enables you to prioritize risks and Am I Affected searches that enable you to look across sources to find dangers.
Additionally, you’ll have access to robust threat intelligence feeds that reveal threat activities and group composition.
Additionally, end-to-end threat management and reporting capabilities guarantee that you have a full picture of your threat environment and can defend against attacks at any step of the threat lifecycle.
If you’re looking for a straightforward platform with simple-to-use, end-to-end threat management capabilities, IBM Security X-Force is a wonderful choice whether you’re a mid-market or large organization across any industry.
Pricing
Please contact the vendor for its pricing.
2. AutoFocus
Palo Alto Networks’ AutoFocus cloud-based threat intelligence technology can help you swiftly identify important threats, analyze them, and take appropriate action without the need for additional IT resources.
To provide you with a thorough picture of possible hazards, the program gathers information from a variety of sources, including the corporate world, foreign spies, and your own network.
It assesses these hazards using machine learning, and it provides the data on an intuitive interface.
One of the finest features of AutoFocus is its ability to produce thorough reports on possible hazards, which can assist you in making more knowledgeable decisions about how to reduce them. Additionally, it can be used by anyone without IT expertise.
Access to Palo Alto Networks’ threat researchers is another benefit of AutoFocus. By way of indications of compromise (IOCs) and thorough threat intelligence reports, they provide more information on possible risks.
The Palo Alto Network threat research team, Unit 42, shares information with AutoFocus regarding the most recent malware attacks.
You can examine the threat report on your dashboard, which gives you further insight into the methods, techniques, and procedures (TTP) used by malicious actors.
Pricing
Please contact the vendor for its pricing.
3. Anomali Threatstream
Anomali is a cybersecurity corporation that focuses on offering intelligence-driven XDR solutions to companies all around the world.
Its potent threat intelligence solution, ThreatStream, uses automation to gather, curate, and disseminate threat data quickly and effectively, giving users accurate and useful information.
The variety of commercial threat streams and tools that can be integrated with the product through the Anomali Preferred Partner (APP) store, along with its machine learning algorithm for scoring IoCs, which aids teams in prioritizing their response to threats, are what really set Anomali apart from its rivals.
The ThreatStream platform gathers threat data from a variety of feeds, such as hundreds of open-source intelligence feeds, paid feeds, Anomali Lab-curated feeds, intelligence from customers’ operational environments, etc.
It then uses machine learning to enhance the data, eliminate false positives, and risk-score IoCs, allowing security teams to quickly prioritize and act on intelligence.
Anomali ThreatStream can be seamlessly integrated with a variety of client security products, including SIEM, EDR, and SOAR. Organizations searching for a strong threat intelligence product that leverages automation and machine learning to gather, analyze, and communicate threats should consider ThreatStream.
Pricing
Please contact the vendor for its pricing.
4. AlienVault USM
AlienVault USM is a comprehensive threat intelligence platform that assists organizations of all sizes in promptly detecting and responding to possible security issues.
AlienVault USM integrates a number of crucial functions, including asset discovery, vulnerability assessment, intrusion detection, behavioral monitoring, and threat intelligence.
Organizations are therefore able to take preventative action to defend against prospective attacks since this gives them a full view of their security posture.
Threat intelligence capabilities are one of AlienVault USM’s standout characteristics. It gathers and examines information from a variety of sources, including open-source intelligence, commercial feeds, and internal security records, to find possible dangers.
By correlating and prioritizing threats using sophisticated analytics, the platform enables organizations to concentrate first on the most important dangers. For security purposes, AlienVault USM offers a single pane of glass.
This entails that security personnel have access to all the data they want in one location, including asset inventories, network activity logs, and real-time danger alerts. Because of this, it is simple to see possible security problems and act quickly to mitigate them.
You can monitor your networks and devices locally or remotely thanks to its unified picture of your company’s security architecture.
Along with SIEM capabilities, host intrusion detection (HIDS), endpoint detection and response (EDR), network intrusion detection (NIDS), and intrusion detection for AWS, Azure, and GCP clouds are also included.
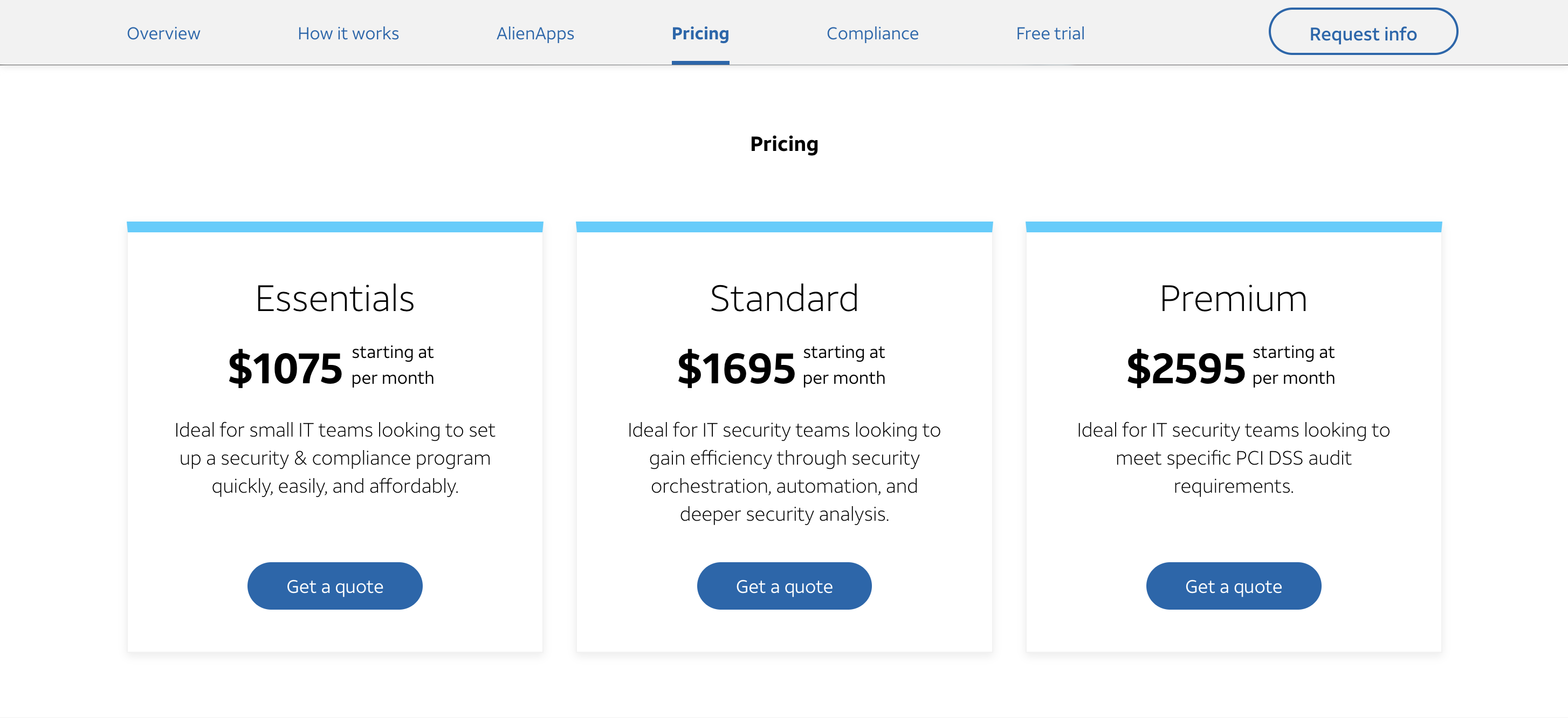
Pricing
The premium pricing of the platform starts from $1075 per month.
5. Crowdstrike Falcon Intelligence
Leading automated threat intelligence platform CrowdStrike Falcon Intelligence aids businesses in staying ahead of possible security risks. Organizations can rapidly and effectively discover, evaluate, and respond to possible risks thanks to the platform’s core features.
The platform analyses massive amounts of data from several sources, including open-source intelligence, dark web surveillance, and malware analysis, using cutting-edge machine learning techniques and artificial intelligence.
This makes it possible for businesses to recognize potential hazards in real-time and respond quickly to mitigate them.
It has its own live feed of threat intelligence. These feeds offer current information on prospective threats, including specifics on threat actors, indications of compromise (IOCs), and attack strategies.
This aids organizations in setting response priorities and implementing preventative security measures.
Moreover, it has reports and dashboards that can be customized. As a result, security personnel can simply see and analyze threat data, monitor important KPIs, and provide comprehensive reports.
Pricing
Please contact the vendor for its pricing.
6. Zerofox
An expert in offering completely managed protection, threat intelligence, and takedown services across a variety of public channels on the surface, deep, and dark web, ZeroFox is a market leader in the brand protection sector.
This is accomplished by delivering accurate information about possible dangers and automatically resolving them using a potent combination of AI, deep learning technology, and its skilled threat-hunting team.
The platform functions by gathering data on the dark web, brands, fraud, malware, vulnerabilities, geopolitical, physical, strategic, and third-party intelligence, and storing petabytes of this data in its “threat data lake”.
After that, this data is examined by AI, machine learning, and human intelligence to provide pertinent and useful threat intelligence. This enables you to carry out limitless takedowns and interruptions, prioritize, and contextualize warnings, as well as enhance threat-hunting skills.
Organizations seeking effective takedown services and trademark protection frequently turn to ZeroFox. The platform is advised for mid-sized to big businesses across all sectors that are especially interested in robust brand protection, top-notch customer service, and in-depth, AI- and human-powered analytics.
Pricing
Please contact the vendor for its pricing.
7. SOCRadar
SOCRadar is a comprehensive cloud-based threat intelligence service that assists organizations in detecting, preventing, and mitigating possible cyber attacks.
The deep and dark web, closed-source feeds, and open-source intelligence (OSINT) are just a few of the sources from which SOCRadar gathers and analyses threat information.
The patterns and abnormalities that point to possible risks are found and identified using cutting-edge machine-learning techniques.
The automatic identification and prioritization of threats by SOCRadar are one of its primary characteristics. Based on the seriousness of the danger and its possible effects on your organization, the platform assigns each threat a risk score.

This enables security teams to focus their response efforts and respond quickly to neutralize high-risk threats. Additionally, SOCRadar provides a configurable dashboard where you can examine and assess threat data in real-time.
It gives a broad picture of your threat environment and includes information on the different threats, their origins, and the degree of danger they pose.
The integration skills of SOCRadar are another important aspect. To offer thorough threat intelligence across your whole security stack, the platform connects with a variety of security technologies, including SIEM, SOAR, and endpoint detection and response (EDR) solutions.
Pricing
Please contact the vendor for its pricing.
8. Flashpoint
FlashPoint’s Threat Intelligence Platform is absolutely something to take into consideration if you’re seeking a reliable method to identify data theft and fraud on the deep and dark web.
Its platform gives users access to deep and dark web intelligence through a combination of automated data collection, machine learning, and human analysis. As a provider of business risk intelligence (BRI), FlashPoint has a reputation for delivering high-quality threat reports and studies.
The ability of FlashPoint to undertake in-depth analyses of the data and chatter from online communities, chat services, forums, and black markets sets it apart from other providers.
They are also skilled at dealing with dangerous people and assisting their customers in getting their stolen items back. Additionally, it provides an analytics dashboard that makes it simple to obtain technical information, intelligence, and automatic editing.
If you’re searching for a platform that can assist you in identifying fraud and stolen data on the deep and dark web and gaining a complete understanding of community activity, FlashPoint’s Intelligence Platform is without a doubt something to take into consideration whether you operate in the public or private sector.
Pricing
Please contact the vendor for its pricing.
9. Digital Shadows
Leading provider of digital risk management services, Digital Shadows specializes in brand protection, cyber threat intelligence, and data exposure.
Its managed solution, SearchLight, offers customers access to top-notch technical, tactical, operational, and strategic threat data while assisting them in managing digital risk, lowering their attack surface, and managing their exposure to threats.
Customers can build up assets, gather threat information from many sources (including the surface, deep, and black web), assess risk, and react to threats using the SearchLight Platform.
The platform also gives users access to the threat intelligence library maintained by Digital Shadows, which has over 10 years’ worth of reports, dark web data, and operational information.
In addition, users can use end-to-end managed takedowns for an extra cost or conduct self-service takedowns when they become aware of data leaks or impersonation attempts as part of the sophisticated brand protection capabilities.
Smaller teams in all sectors can benefit greatly from Digital Shadows’ SearchLight, which offers strong brand protection capabilities and threat data from a variety of sources.
Pricing
Please contact the vendor for its pricing.
10. Recorded Future Intelligent Platform
Global threat intelligence service Recorded Future focuses on fusing human experience with automated, AI-powered data collecting to help organizations more effectively spot, disrupt, and address risks.
The platform provides unmatched access to open-source intelligence, including technical sources and information gleaned from the dark web.
Expert analysts and Recorded Future’s “Intelligence Graph” work together to curate intelligence findings. The Intelligence Graph regularly updates billions of new entities in real-time and can detail danger data going back over 10 years.
A type of malware and the vulnerabilities it targets, for example, can be connected through the platform’s natural language processing capacity, which provides pertinent, useful intelligence.
The organization, SecOps, threat, vulnerability, third-party, geopolitical, identity, card fraud, and attack surface intelligence modules make up the Recorded Future platform.
It also offers extra add-ons for takedown services and on-demand analysts. This modular design makes it simple to connect the solution across many teams and responsibilities and to give each group of people the pertinent information for their position.
For bigger businesses seeking in-depth open-source intelligence from a variety of sources, the Recorded Future Intelligence Platform is a fantastic choice.
Pricing
Please contact the vendor for its pricing.
Conclusion
In conclusion, we must alter our defense measures as cyber threats develop. Threat intelligence solutions fill this need by providing IT teams with access to the collective wisdom of the world’s cybersecurity community.
These platforms refresh their data feeds often with current information from specialists and organizations throughout the globe, keeping you informed about potential attack variations even if you haven’t directly met them.
Additionally, they can even aid in anticipating and thwarting the most harmful zero-day assaults before they can do any harm when linked with security technologies like SIEM.





Leave a Reply