We have all arrived at an intriguing historical turning point thanks to the digital revolution.
With several channels for easing information sharing and transactions among people, communication is no longer a problem in the modern world.
In essence, the digital world is gradually evolving into a virtualized version of the real world.
The digital world, like the physical world, uses user names and accounts to establish identification. Therefore, it is crucial to consider the methods used for digital identity in the present.
One of the newest ideas in digital identification, self-sovereign identity, or SSI, has been receiving prominence lately.
We shall examine self-sovereign identification in detail in this post, including its benefits, workings, and other aspects.
So, what is Self-Sovereign Identity?
A user-centric approach to digital identification called Self-Sovereign Identity (SSI) allows individuals and businesses complete control over their data.
As a consequence, SSI makes it possible for anybody to securely confirm their identity (i.e., who they are and anything about them) and exchange their data effortlessly without compromising security or privacy.
To put it another way, SSI gives you the ability to “bring your own identity,” and this is true for pretty much any kind of information, including your basic information (like name, age, and address) as well as details about your education and employment background, your health and insurance coverage, your bank account and financial situation, etc.
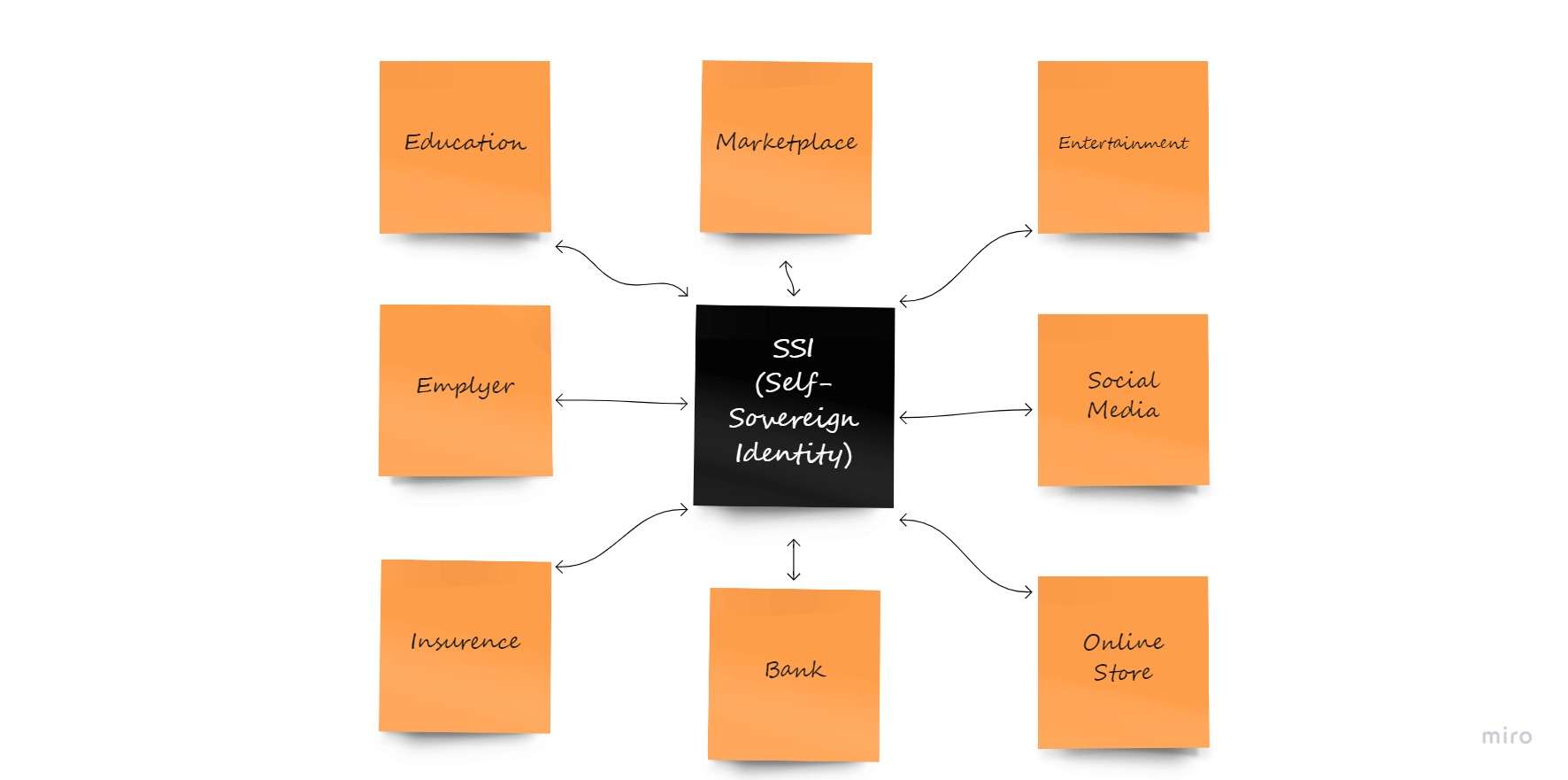
Additionally, SSI can be used to represent the digital identities of organizations, objects, and individuals in addition to people (IoT).
In the end, SSI ensures a digital setting where communication is straightforward and stress-free.
It is only the following evolutionary step in identity management, a new paradigm in which our digital identities are no longer divided and locked into silos that are under the authority of someone else but are instead exclusively at our own disposal to be exchanged safely and discreetly.
Why should you adopt a Self-Sovereign Identity?
We have been watching a worldwide and cross-industry digitalization movement for several decades.
While this process began slowly, it accelerated with the introduction of cellphones, which put the digital world in our pockets, and more dramatically with the breakout of COVID, which drove the world to shift from in-person encounters to digital ones.
However, it is no secret that the internet was constructed without an identity layer, so as the world becomes increasingly digital, we are presented with apparently insurmountable challenges.
In other words, while digitization offers numerous benefits, it has a cost:
- Issues with privacy: We saw privacy scandals and declining trust in data aggregators as a result of people not having control over their data.
- Security problems: Traditional methods of protecting user data and access to services, especially password-based authentication, have proven to be ineffective and resulted in innumerable significant data breaches.
- a lack of data control: Few firms have a concentrated amount of power, and they successfully manage data and lock in people.
- Issues with compliance: Because they must centrally store and handle user data, online service providers are subject to governmental oversight.
- terrible user experience: Users are compelled to manage a variety of authentication procedures (such as passwords) and endure protracted online identifying procedures.
SSI offers to overcome these issues by giving consumers ownership over their data and allowing them to share it easily, anonymously, securely, and on their terms.
Benefits for persons
SSI allows secure, hassle-free digital connections and gives consumers ownership over their data:
- Control: People can fully choose how their data is stored, accessed, and portable because of SSI’s user-centric design.
- Consumer encounter: The sharing of data with others is made simple via SSI. Simple one-click experiences are used instead of more conventional data exchange methods like forms and uploads.
- Independence: People are no longer locked in since they have data portability and can take their data with them wherever they go when they have control over their data.
- Privacy: Privacy is guaranteed by SSI’s user-centered design, support for selective disclosure, and other data minimization methods.
- Security: By removing key attack vectors like passwords or centralized data storage, SSI reduces the danger of data breaches or leaks.
- dependable interactions: Making potentially any form of data verifiable in order to combat fraud and fraud, including identity theft, is one of SSI’s greatest benefits.
Benefits for organization
SSI enables businesses to enhance their offerings, streamline their operations, and reduce numerous business risks:
- Fraud avoidance: SPAM, identity theft, document forgery, and other forms of hostile activity can all be stopped by organizations.
- Data integrity: Organizations can obtain trustworthy information on their stakeholders through SSI, which is validated and signed by dependable outside parties.
- Compliance: As a result of user-centric data and permission management, organizations automatically abide by privacy and data protection rules.
- Security: By removing risk factors like passwords and bulk data storage, organizations can reduce the likelihood of data breaches or possibly avoid them altogether.
- Conversion and satisfaction among stakeholders: Organizations can provide their stakeholders with more convenient access to their services or goods, increasing conversion rates, lowering help desk calls, and improving stakeholder satisfaction overall.
What is the mechanism of Self-Sovereign Identity?
You must take into account two viewpoints in order to conceptualize SSI and comprehend how it operates.
The functional approach, focuses on comprehending the effects of SSI on its users and the market, especially what SSI makes possible (that could not be done without SSI).
The technical approach is concerned with comprehending the technologies upon which SSI is based, as well as the qualities of those technologies that give birth to SSI’s functioning in the first place.
Functional approach
With the aid of SSI, we are able to simulate digital identity in a manner similar to how it functions in the physical world, which is based on paper identification cards and papers.
There are only a few little changes.
For instance, rather than being made of paper or plastic, our identification documents are now digital credentials comprised of bits and bytes, and instead of being kept in leather wallets, they are kept in digital wallets on our phones.
The fact that these digital credentials can be accurately validated by anybody with whom they are exchanged, online or offline, is significant.
SSI makes it possible for decentralized ecosystems where many parties can share and verify data pertaining to identities.
Every party can play three roles in these ecosystems, which resemble three-sided marketplaces:
- The issuers: parties that “issue” digital credentials containing identity-related data to individuals or groups (referred to as “Holders”). They are an SSI ecosystem’s initial data sources. For instance, a government can provide digital passports to its residents or graduates can get digital diplomas from universities.
- The holders: digital credentials that are issued to people or organizations (“Issuers”) and contain information about the issuer. Holders can create comprehensive digital identities that are in their control and that are simple to share with others by collecting and keeping such credentials in digital wallets (“Verifiers”).
- Verifiers: Data given by third parties (“Holders”) that are used by other parties to supply goods and services can be reliably verified and processed by those parties. Oftentimes, organizations or people acting in their official capacities are the “Relying Parties,” also known as “Verifiers.”
Three responsibilities are necessary for SSI ecosystems:
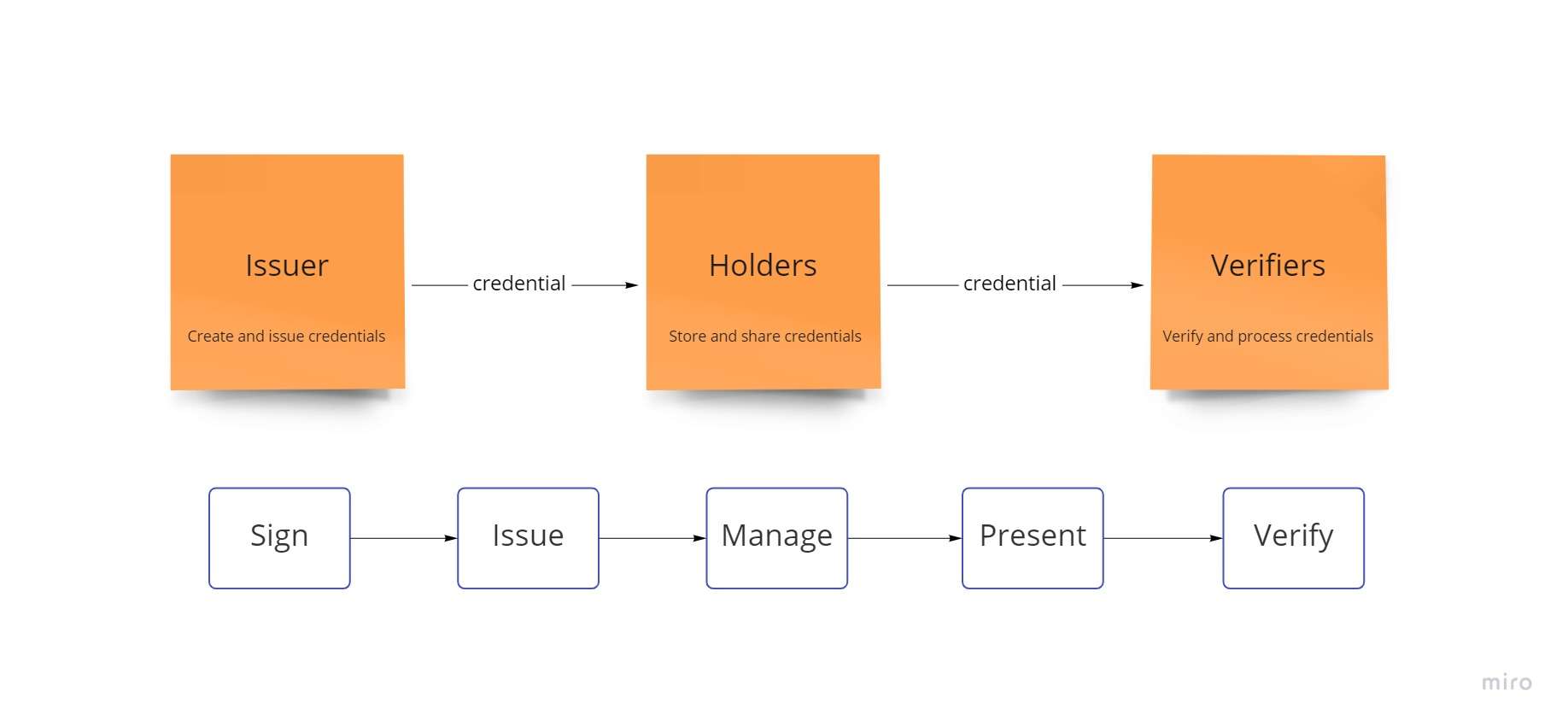
Depending on the use case, a single party can take on the roles of Issuer, Holder, and Verifier. For instance, a university could provide degrees to graduates (Issuer), maintain its own accreditations (Holder), and ask prospective students for their academic records (Verifier).
Technical approach
From a technology standpoint, comprehending SSI necessitates having a basic grasp of the following concepts:
- Decentralized Identifiers (DIDs), establish a public key infrastructure by connecting keys to distinctive identifiers that permit various parties to locate and communicate with one another.
- Trust Registries can act as a reliable source for information sharing. Alternatively said, they act as a “layer of trust” and a “single source of truth.”
- Cryptographic keys, enable essential features like encryption and authentication while still giving users control over their digital identities.
- Wallets, which enable the administration and exchange of our digital identities and data through simple apps, save our keys (control) and VCs (identification data) and store our identity data and keys.
- Credentials You Can Check (VCs) which are digital identification papers that can be shared with anybody and securely checked for (validity, integrity, authenticity, and provenance) while maintaining privacy. They are never kept on a blockchain, which is significant for privacy and regulatory reasons.
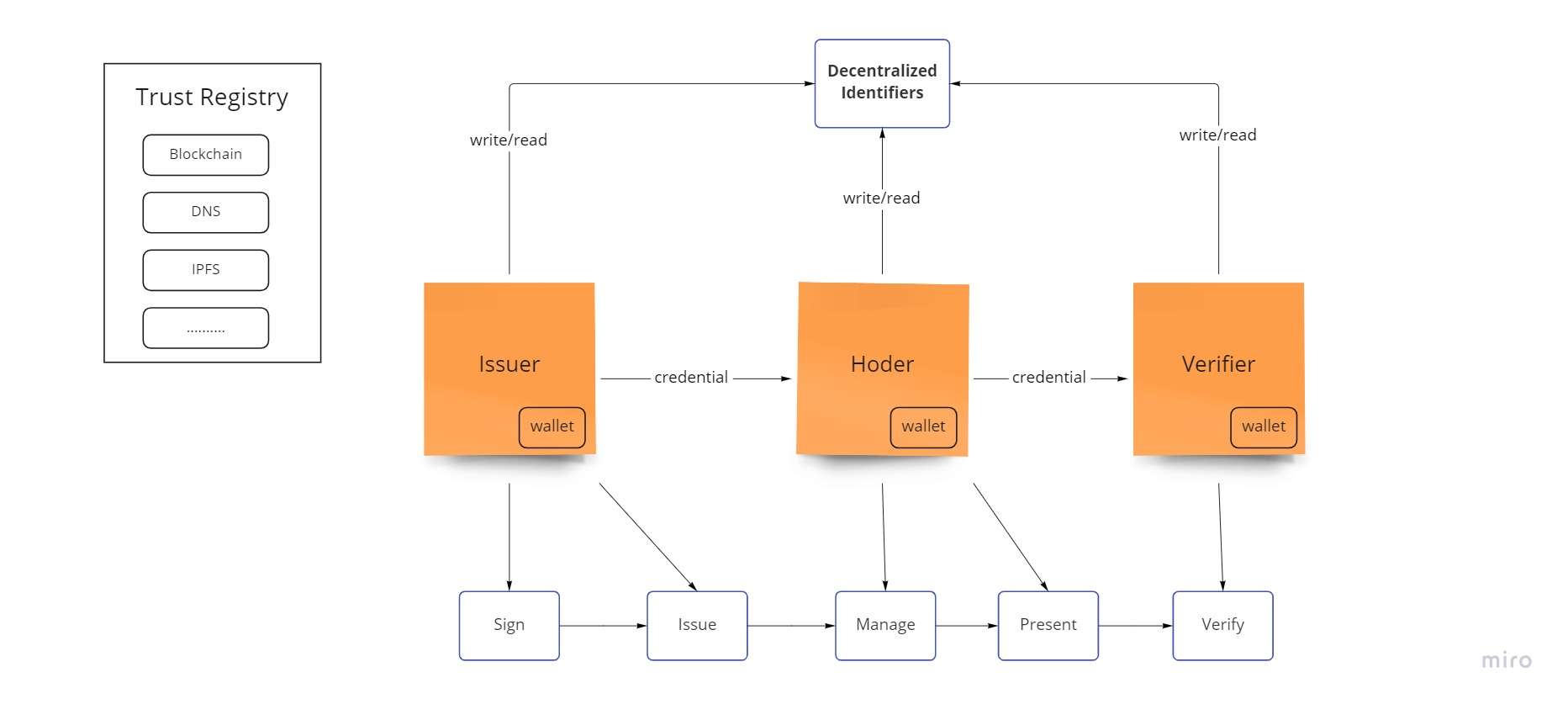
Trust Registries can be created using a variety of technologies, such as blockchains (EBSI, Ethereum), or the domain name service (DNS). SSI even operates solely on a peer-to-peer basis without any Trust Registries (for specific use cases).
Similar variations in DID types, keys, evidence, credential formats, authentication methods, and data sharing protocols are possible.
As a result, there are several “flavors” of SSI based on the varied ways that the various building components have been combined.
The disparities in the technologies employed serve as an important illustration of why interoperability has always been one of the industry’s most crucial issues and why using open standards—such as those created by the W3C, Decentralized Identity Foundation, OpenID Foundation, and others—is essential for choosing technologies and vendors.
Use cases
Every company and every government should value digital identification. There isn’t a field or industry out there that wouldn’t need it. The usage scenarios are therefore limitless.
Examples include formal identification credentials needed for travel or KYC (“know your customer”), as well as degrees and certificates needed to provide certain services or social information for designing more personalized and distinctive experiences.
Pros
- Data is more confidential.
- The method is more effective.
- Data that belongs to users is more in their hands.
- It is more secure and guards against frequent data breaches and other assaults.
- It is not necessary for users to rely on other identity providers that could market and profit from your data.
Cons
- Users are in charge of their own safety.
- It might be difficult to keep track of personal information and permits.
- Proof data is frequently unorganized and readily fabricated.
- It’s possible that certain data intermediates can’t be eliminated.
- There may be many identification platforms, which would need consumers to utilize various applications.
Conclusion
As a result, SSI is unquestionably a concept with a bright future since it deals with problems that are relevant to all sectors and are universal.
As more businesses use SSI, the acceptance of the technology will spread like wildfire, eventually bringing about widespread SSI.




Leave a Reply