For decades, there have been two approaches to cybersecurity: endpoint-based and network-based.
Then came cloud computing, and we simply lifted and transferred to the cloud, supplementing those methodologies with cloud security posture managers (CSPMs), which looked exclusively at the cloud setup.
The two fundamental problems with this patchwork of CSPMs and agent-based technologies, now called CWPPs, are as follows.
Agents do not, in the first place, work for the cloud. They cause a lot of conflict inside the company and have a high TCO. Even worse, ephemeral workloads can only endure a short while before an agent can awaken and begin functioning.
The second issue with this compartmentalized strategy is that each security instrument only sees its own piece of the jigsaw, which places an enormous strain on already overworked security practitioners who try to fit everything together manually – which never works
I’m thinking of one vendor who made a concerted effort to conceal the fact that their CSPM + CWPP package is a patchwork of inconsistent point solutions.
Orca offers a unified SaaS-based platform for managing compliance, managing vulnerabilities, managing cloud security posture, and protecting workload and data.
In this article, we’ll talk about Orca security, including its key features, advantages, and ability to converge cloud security across the whole application lifecycle.
So, what is Orca Security?
A cloud-native security platform is called Orca Security (CNAPP). Cloud security posture management (CSPM), cloud workload protection platform (CWPP), container scanning, and cloud identity and entitlement management (CIEM) technologies are all combined to simplify cloud security across AWS, Azure, and Google Cloud.
Without the requirement for an agent, the platform can be deployed throughout your cloud infrastructure, minimizing the impact on your performance.
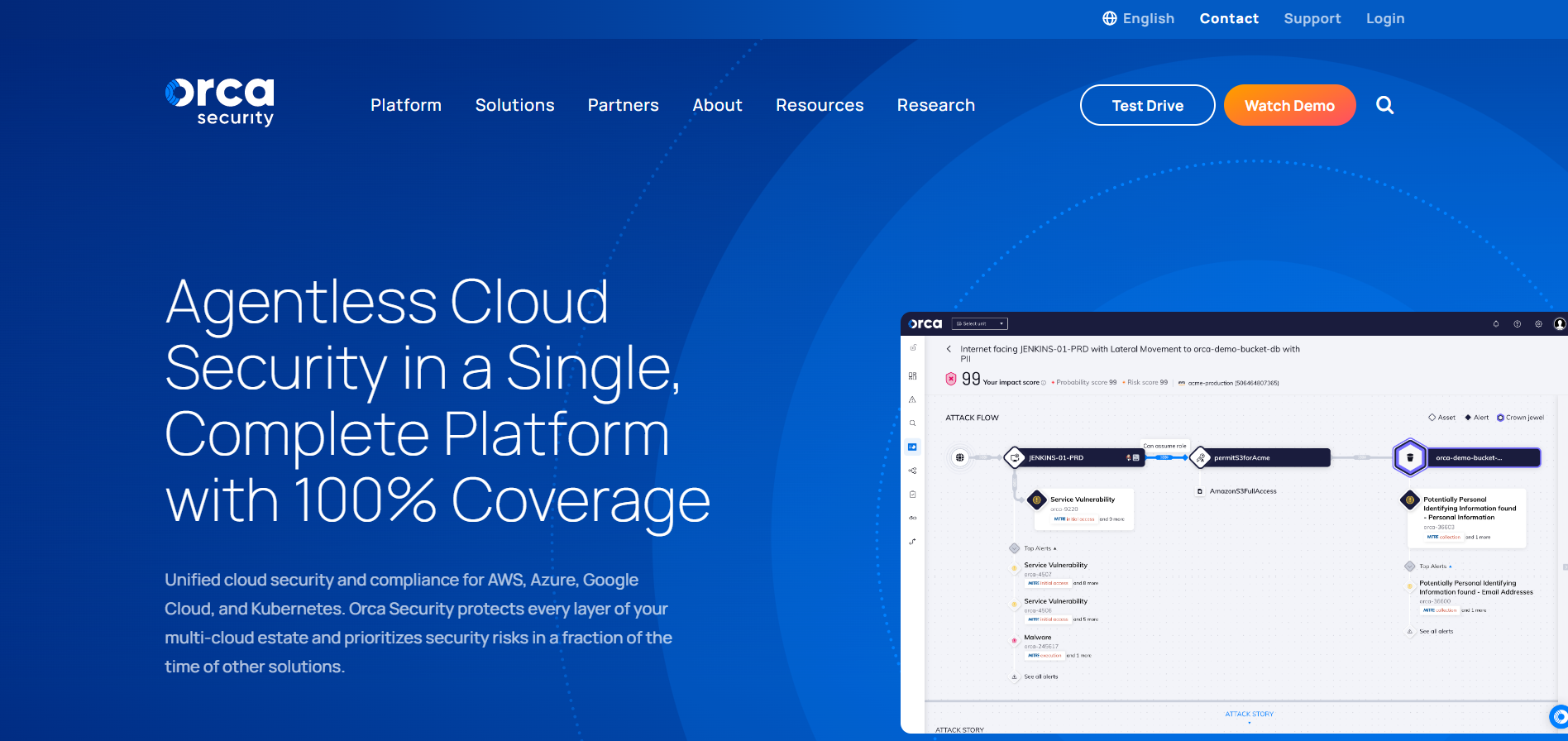
In the CNAPP sector, Orca is a pioneer in integrating CSPM, CWPP, and vulnerability management capabilities into its platform. Through its no-code platform, it now offers a few services, including:
- With SideScanning, Orca builds an inventory of the software in your cloud environment, enabling scans to find known vulnerabilities in its Vulnerability Database, which incorporates information from more than 20 data sources.
- In order to find configuration errors in your cloud environment and compare them with a set of configuration constraints, Orca Security uses configuration information from workloads and cloud accounts.
With the aid of signature-based detection as well as cutting-edge heuristic techniques like file analysis, file emulation, and generic signature detection, the solution completely covers your cloud for malware.
The solution continually checks your public cloud for widespread Identity and Access Management (IAM) misconfigurations.
It searches your cloud for information that attackers may exploit, such as exposed keys, passwords stored in shell history, vulnerabilities, and other items.
Finally, it does a thorough inventory of all of your public cloud resources, including cloud workload software inventories.
Additionally, it does an asset inventory of the data and network resources available on your cloud infrastructures platforms, such as storage buckets, security groups, accounts, photographs, cloud services, and more.
Features
- CSPM, CWPP, CIEM, and KSPM solution capabilities are combined into one simplified platform by CNAPPs.
- CNAPPs integrate information from deep inside the workload with specifics of the cloud architecture to instantly identify and rank the most important security threats at every level of the technological stack.
- The context-aware engine of Orca prioritizes security alarms according to their importance, exposure, and potential business effect.
- With CNAPPs, the emphasis is shifted from narrow, unrelated, individual security concerns to larger, related groups of issues that are most dangerous to your company.
- Without extra installation, Orca instantly recognizes and keeps track of any new cloud assets you upload.
Orca’s Cloud Security for the Entire Application Lifecycle
Security leaders are in charge of all areas of security governance, including making sure that applications are thoroughly tested and secure in production.
Orca Security secures Shift Left Security capabilities throughout the Build, Deploy, and Run phases of the software development lifecycle to assist businesses in detecting important risks and meeting compliance mandates:
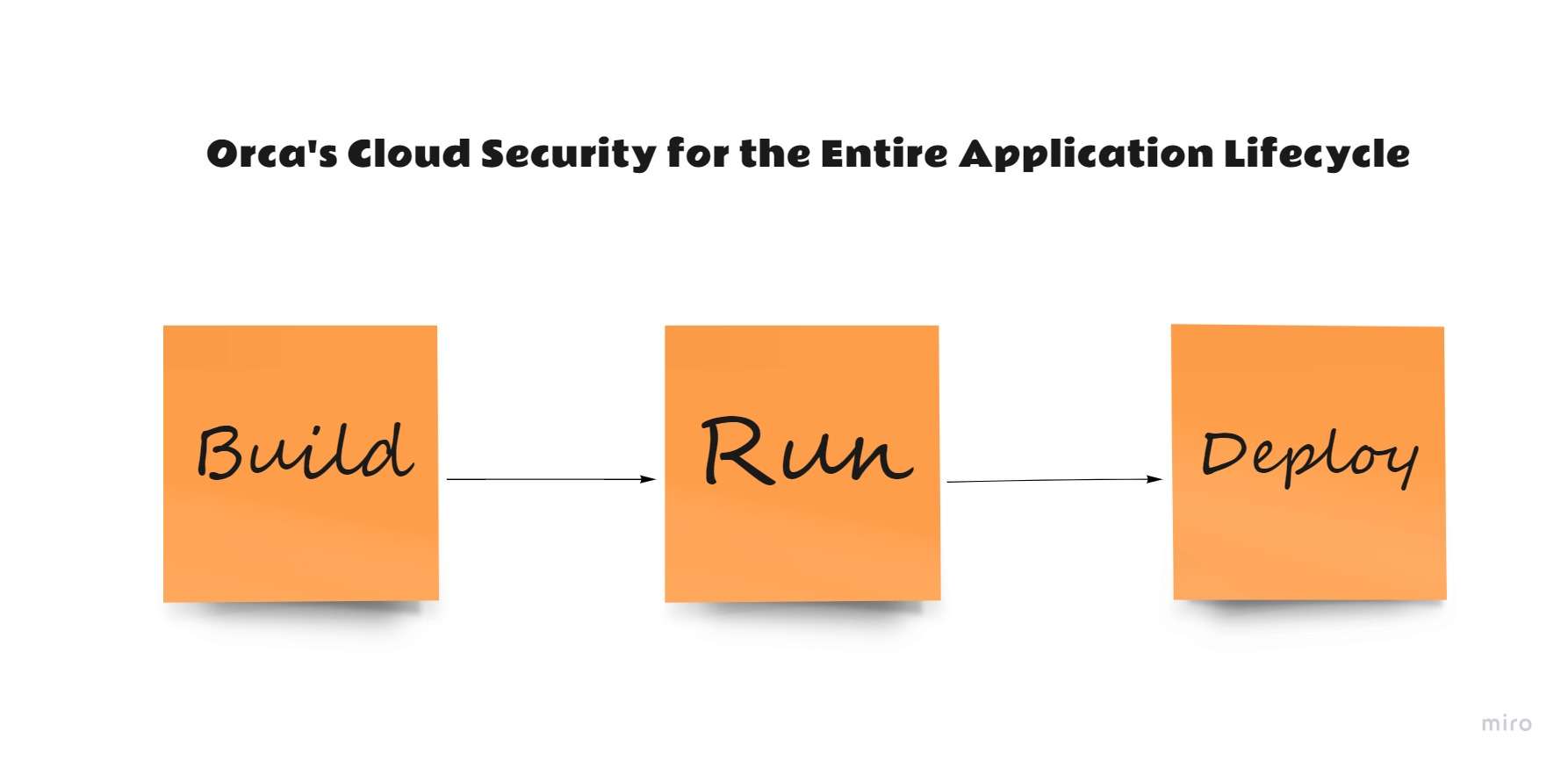
Build
Container images and IaC templates are inspected for vulnerabilities and misconfigurations on the developer desktop or as part of regular, continuous integration and continuous delivery (CI/CD) operations.
This context-aware approach considers both the current run time environment and the deployed code to provide a significant boost in accuracy.
Deploy:
Registries are regularly checked, and guardrail regulations are in place to stop unsafe deployments and to guarantee that application artifacts are secure before being deployed.
When private keys are discovered as part of a CI scan, which might enable lateral movement inside a cloud estate, continuous monitoring also identifies these secrets.
Run:
Additionally, contextual and prioritized warnings are used to monitor risks in production environments. Risks are immediately remedied, and data is integrated with contemporary ticketing and alerting technologies.
Benefits
- No-code management tool for your cloud environment
- Create a graph that includes all of your cloud resources, software, connection, and trust to rank risk.
- A SaaS-based cloud security platform for workload and data protection, managing cloud security posture, managing vulnerabilities, and managing compliance can streamline SecOps.
- External data is gathered through side scanning. This contrasts with parasitic organisms that reside within your workload. Using read-only access to the runtime block storage used by the applications, Orca can quickly develop a comprehensive risk assessment of your cloud estate.
- To create a visual risk context map of your whole cloud estate, Orca blends workload-deep intelligence with metadata from cloud configurations. You are then able to immediately identify any potential crucial attack routes.
- Orca’s SideScanning enables you to obtain total visibility and coverage without executing any code or transmitting a single packet over the network. There is no downtime as a result, and neither users nor workloads are affected.
How Orca Security can assist you with cloud security?
Security executives can benefit from Orca Security’s agentless side-scanning technology, which gives a complete insight into the whole cloud ecosystem in a matter of minutes with a single comprehensive platform.
What is in the cloud or multi-cloud environment and where is it located are addressed by this. This cutting-edge approach to cloud security technology aids DevOps in locating frequent configuration errors, compliance incidents, and crucial security flaws that present the greatest risks to the company.
Without the need to install agents, the Orca Security platform installs across different cloud ecosystems in minutes, easing the strain on security teams, lowering enterprise cyber risk, and enhancing overall cloud hygiene and visibility.
Conclusion
In conclusion, Orca created a ground-breaking new technology called SideScanning in response to the drawbacks of agents and network scanners that delves deeply into the workload without the limitations and operating expenses of existing old technologies.
Instead, it gathers information out-of-band from the workload’s runtime block storage and directly from the cloud provider’s API in the form of a CSPM.
As a consequence, with this method, we don’t need to run any code or send any packets into your environment.
After a quick and simple one-time deployment, Orca surfaces the most important risks for both the workload and the cloud configuration itself, guaranteeing 100% coverage.
These risks include vulnerabilities, malware, misconfigurations, weak and leaked passwords, lateral movement risk, misplaced PII, and more.





Leave a Reply